What Is Packet Sniffing complete guide will be described in this article. Packet sniffing energy sound strange in a cyber security context, but rest guaranteed that it doesn’t involve your nose one bit. Learn what packet sniffing means, how it’s used legally and illegally, and the different types of packet sniffing attacks. Then, start using a reliable VPN to help protect your online activity and the data you share against sniffing attacks and other privacy threats.
What is packet sniffing?
Packet sniffing is a method of detecting and assessing packet data sent over a network. It can be used by administrators for network monitoring and security. However, packet sniffing tools can also be used by hackers to spy or steal confidential data.
The packet sniffing process is achieved by analyzing data packets sent through Transmission Control Protocol/Internet Protocol (TCP/IP) — the protocol that connects devices to wired or wireless networks. These data packets can include different types of traffic sent across a network, such as login details and passwords, as well as technical data like IP addresses.
IT professionals use packet sniffers for network troubleshooting by checking for harmful data packets. They also gain insights around bandwidth usage — for example, revealing which applications are the most intensive — to detect hidden issues affecting network performance.
Network administrators can also use packet sniffers to “sniff” websites that are being visited, the type of content being consumed, and communications like email.
Is packet sniffing legal?
Packet sniffing is legal for the purposes of network management and when used only on the part of the network for which the person or organization conducting the sniffing is responsible. Packet sniffing is illegal when access to data packets is unauthorized. Hackers use packet sniffing to monitor and steal data, which is also an illegal use of packet sniffing.
How does packet sniffing work?
Packet sniffers can be a piece of hardware or software that work by observing data moving between networked computers and between those devices and the internet. Sniffers are sometimes referred to as packet analyzers or network analyzers.
Typically, networks send and receive data as packets — segments of broken down information — to make it quicker and easier to manage. Then, the information is reassembled from the packets once the transfer is complete.
Devices connected to a specific network hub observe all data packets moving through the network and simply disregard any packets that aren’t intended for that destination. A packet sniffer is not configured in the same way and instead can receive all packets.
Some larger networks are “switched” — meaning they use a network switch to forward specific data only to the designated device, rather than to all network devices. Sniffing on a switched network requires additional protocols to ensure the packet sniffer can be monitored.
There are two main types of packet sniffing in cybersecurity:
· Hardware packet sniffing uses a physical device that plugs directly into a network interface — that is, the connection point between your computer and a network. This method is favored by IT experts who want to access specific parts of a network.
· Software packet sniffing uses a program to capture all traffic sent across the network. This type is much more popular today than hardware packet sniffing.
Users can also decide whether they wish for all data packets to be captured and analyzed at a later date (known as unfiltered packet sniffing) or opt to capture only data packets that meet specific criteria (known as filtered packet sniffing).
What is a packet sniffing attack?
A sniffing attack is when a hacker uses a packet sniffer to capture and access confidential, unencrypted data packets for malicious purposes. This type of data can include both personal data (name, address, telephone number) and financial information (banking details and login credentials).
Without robust cybersecurity tools, malicious packet sniffing can be used to conduct further attacks, such as ARP or DNS spoofing, or inserting malicious code into data packets via SQL injection. If you accidentally download & the infected file from the web or open an attachment corrupted with malware, a packet sniffer could get installed on your device.
How does a packet sniffing attack work?
A packet sniffing attack works by a hacker using a sniffer to maliciously capture and read data flowing through a network. Targeted data packets usually include account information, personal information, or private messages.
Packet sniffing attacks are either active or passive:
· Passive sniffing: When several devices are connected to your Local Area Network (LAN) or wireless network, a hacker could connect too and passively monitor traffic going through this hub. This type of packet sniffing can be very difficult to detect — think of it like covert spying or wiretapping.
· Active sniffing: This method is used on switched networks, where only the packet’s destination can receive the data. Hackers need to get around this and do so by adding traffic to the network.
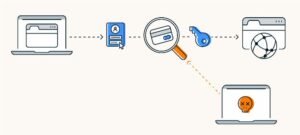
An illustration showing how packet sniffers can steal data from a network.Packet sniffers secretly collect data traveling between network devices and the internet.
Why do hackers use packet sniffers?
Hackers use packet sniffing attacks for many reasons, such as recording your online activities, reading your emails, and viewing your passwords and banking details. Packet sniffers allow an attacker to spy on you, gaining valuable information about any aspect of your life that is managed or shared online.
Aside from breaching your privacy, the information a hacker can gain from packet sniffing can be used to conduct further attacks, including:
· Infecting a network with viruses or malware
· Holding important files hostage using ransomware
· Accessing your accounts to steal money and service subscriptions
· Using information to aid an attack on an organization, such as your employer
Types of packet sniffing attacks
Here are some of the different types of packet sniffing methods and techniques that hackers use:
Wi-Fi packet sniffing
Do you ever need to connect to free public Wi-Fi in a coffee shop, caravan station, or city center while traveling? Hackers can deploy a Wi-Fi sniffer on an unsecured network to monitor data moving through it, making any device connected to the Wi-Fi more vulnerable to prying eyes.
Packet sniffing is just one reason to avoid accessing unsecured Wi-Fi without a VPN. Avast SecureLine VPN encrypts your internet data, helping to protect your IP address and personal network traffic from sniffers.
Browser history sniffing
Your internet browser can store certain information, such as saved form data or login details. While this can be convenient for signing into your favorite sites, hackers can take advantage of this using packet sniffing. And Google saves some browsing data even after you delete browser cookies and history.
JavaScript sniffers
In a JavaScript sniffing attack, malicious script can be inserted into a website to capture your private information as you enter it on the website or an online form. This code can be used to intercept phone numbers, email addresses, bank details, passwords, and more. Also check UX Analytics Tools
Session hijacking
Also known as TCP session hijacking, this method of packet sniffing allows a hacker to obtain your session ID — an individual number that a server provides each user when they visit a site during an online session. By hijacking a legitimate session ID, a hacker can then complete “authorized” activity on the network for nefarious purposes.
Password packet sniffing
Password sniffing is used to capture unencrypted data packets that contain password information. This is a type of Man-in-the-middle attack wherein the hacker steals data as it moves between your device and its destination.
Domain Name System (DNS) poisoning
DNS poisoning — a sophisticated, large-scale form of pharming — can allow hackers to reroute internet traffic from a legitimate website to a convincing fake website. As these websites are remarkably similar, users can easily be tricked into entering login credentials like they normally would on the real site.
Address resolution protocol (ARP) sniffing
Address resolution protocol (ARP) ordinarily works by changing addresses between various networks. This includes transforming an IP address (your internet address, which can be identified globally) to a media access control (MAC) address, the address unique to the device you’re using.
Also known as ARP spoofing, ARP cache poisoning, and ARP poison routing — ARP sniffing allows hackers to intercept data packets and send false messages on your network, redirecting traffic away from your IP address to their own. It’s often combined with other attacks, such as Man-in-the-middle attacks or session hijacking attacks.
Dynamic Host Configuration Protocol (DHCP) sniffing
The Dynamic Host Configuration Protocol (DHCP) gives an IP address to a device connecting to a network. During a DHCP packet sniffing attack, or DHCP snooping attack, hackers set up their own rogue DHCP server by flooding the real one with multiple requests for IP addresses until it can’t distribute more. The rogue DHCP then takes its place, enabling packet sniffers to monitor data flowing along the network.
Every packet sniffer captures data packets that travel through a networkEvery type of packet sniffer captures data packets that travel through a network.
Examples of packet sniffing attacks
· Heartland Payment Systems data breach (2009)
An American payments processing company, Heartland Payment Systems was attacked with malware that allowed the sensitive financial information of their customers to be sniffed as the data crossed the network. The breach cost the company $12.6 million.
· Flame (2012)
Flame is a sophisticated type of malware that includes a sniffer. The packet sniffer has captured vast amounts of confidential data, including screenshots and audio files from countries in the Middle East. Flame is thought to be a form of state-sponsored espionage or cyber warfare, though the exact origin remains unknown.
· APT28 attack on hotel guests (2017)
A Russian hacking group known as APT28, or “Fancy Bear,” used Wi-Fi sniffing to steal usernames, passwords, and other data from hotel guests in Europe and the Middle East. The attack also used malware and EternalBlue, which exploited vulnerabilities in Windows.
More recently, in 2021, APT28 was also found to spread malware through unpatched vulnerabilities in Cisco routers. Also check Cxtsoftware Alternatives
· BIOPASS RAT (2021)
This started as a watering hole attack (in which frequently visited websites are compromised) on Chinese online gambling companies. Using social engineering, hackers tricked website users into downloading software that contained the weaponized software tool Cobalt Blue, or BIOPASS RAT, a remote access Trojan. The infected software allowed hackers to sniff data from their victims using Open Broadcaster Software (OBS) Studio, a video and live-streaming app.
What is the best defense against packet sniffing?
Here are several ways that can help protect your network from unwanted packet sniffing:
· Keep software updated. Regularly update your software & operating systems to patch vulnerabilities and prevent them from being exploited by different types of hackers.
· Use extra login security. Create strong passwords and enable additional authentication tools, such as two-factor authentication for additional layers of protection.
· Use caution when opening emails from unrecognized addresses. Don’t click strange attachments or links, because they could be part of a phishing campaign that leads to a packet sniffing attack.
· Connect to the internet with a VPN. Employing a Virtual Private Network (VPN) while scanning the web sends your data through an encrypted tunnel, shielding your online activity. This is particularly important when accessing public Wi-Fi, which usually has weaker protections that may increase the risk of a packet sniffing attack.
· Only visit secure websites. Ensure the areas you visit are secured with the HTTPS protocol, as sites with the HTTP protocol offer less protection. These days, most browsers flag unsecured websites in the address bar before you visit.
Protect your network with Avast SecureLine VPN
Help secure your network against packet sniffing and protect your personal information with Avast SecureLine VPN. Built on OpenVPN and OpenSSL — the most reliable privacy protection protocols — your data is shielded from unwanted third parties that could be trying to collect and harvest data. Try Avast SecureLine VPN today and keep your network connections and personal data private.